DPRK Analysis
DPRK AnalysisSmile, You're on Camera: A Live Stream from Inside Lazarus Group's IT Workers Scheme
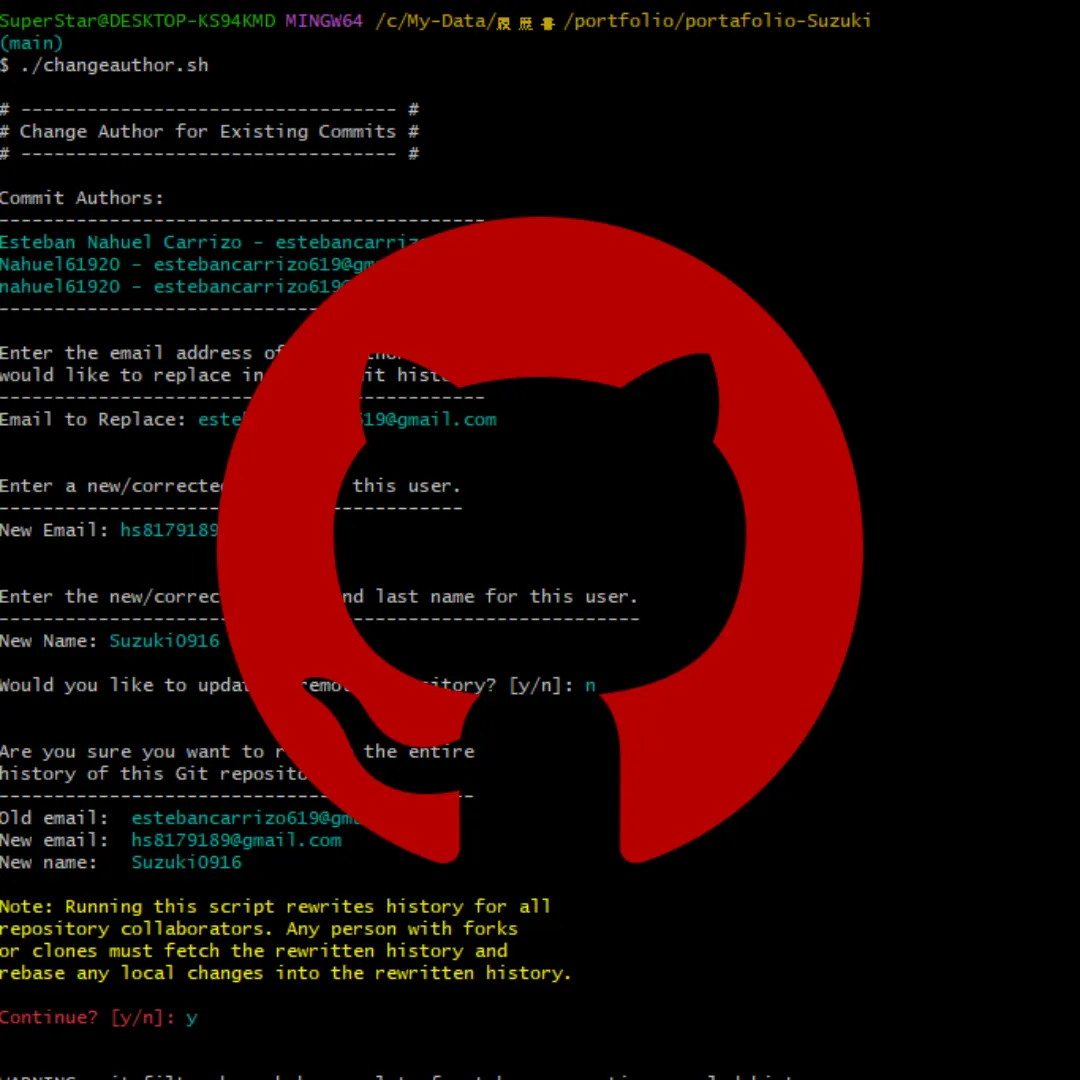
Unprecedented investigation capturing North Korean IT workers live on camera through sandboxed laptop farms, documenting their recruitment tactics, toolchain, and infiltration operations in real-time.